禁用Kubernetes集群中的DES加密算法

背景
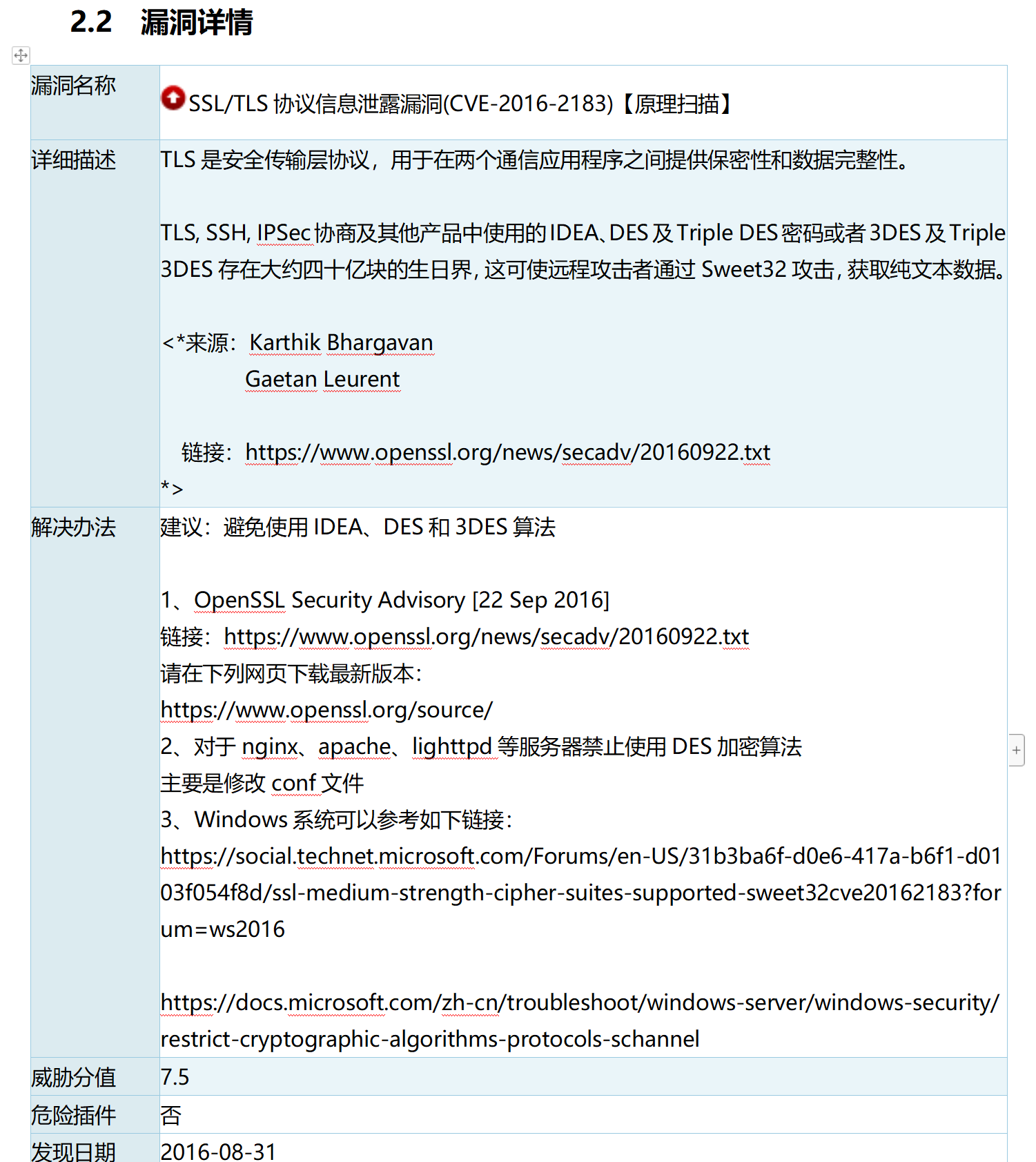
在等保扫描检测时,提示SSL/TLS协议信息泄露漏洞(CVE-2016-2183),安全级别为高--必须整改。然而对应的端口皆为Kubernetes的各组件服务。端口、服务对应如下:
系统环境
- 操作系统:银河麒麟v10
- Kubernetes: v1.20.15
检测工具
- nmap
- openssl
上述任选一种即可,建议使用namp,更为直观。
安装摘要
# wget https://nmap.org/dist/nmap-7.93-1.x86_64.rpm
# yum -y localinstall nmap-7.93-1.x86_64.rpm
# nmap -version
Nmap version 7.93 ( https://nmap.org )
Platform: x86_64-redhat-linux-gnu
Compiled with: nmap-liblua-5.3.6 openssl-3.0.5 nmap-libssh2-1.10.0 nmap-libz-1.2.12 nmap-libpcre-7.6 nmap-libpcap-1.10.1 nmap-libdnet-1.12 ipv6
Compiled without:
Available nsock engines: epoll poll select
环境检测
APIServer
[root@kube-master-1 ~]# nmap --script ssl-enum-ciphers 127.0.0.1 -p 6443
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-10 11:37 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000090s latency).
PORT STATE SERVICE
6443/tcp open sun-sr-https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (secp256r1) - C
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (secp256r1) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| compressors:
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| TLSv1.3:
| ciphers:
| TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| cipher preference: client
|_ least strength: C
Nmap done: 1 IP address (1 host up) scanned in 0.38 seconds
或者使用openssl工具
# openssl s_client -connect 127.0.0.1:6443
<输出略>
整改过程
Etcd
如果k8s集群中的etcd服务是使用kubeadm部署的,可以按下面方法来处理
# vim /etc/kubernetes/manifests/etcd.yaml
- --cipher-suites=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 # 33行
如果单独部署etcd,则可以在配置文件中加入以下:
ETCD_CIPHER_SUITES=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
APIServer
编辑 kube-apiserver 配置文件 /etc/kubernetes/manifests/kube-apiserver.yaml
42 - --tls-cert-file=/etc/kubernetes/pki/apiserver.crt
43 - --tls-private-key-file=/etc/kubernetes/pki/apiserver.key
44 - --tls-cipher-suites=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 # 新增
Controller-Manager
编辑 kube-controller 配置文件 /etc/kubernetes/manifests/kube-controller-manager.yaml
# vim /etc/kubernetes/manifests/kube-controller-manager.yaml
<省略若干行>
28 - --root-ca-file=/etc/kubernetes/pki/ca.crt
29 - --service-account-private-key-file=/etc/kubernetes/pki/sa.key
30 - --tls-cipher-suites=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 # 新增
Scheduler
编辑 kube-scheduler 配置文件 /etc/kubernetes/manifests/kube-scheduler.yaml
# vim /etc/kubernetes/manifests/kube-scheduler.yaml
<省略若干行>
18 - --leader-elect=true
19 - --tls-cipher-suites=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
kubelet
编辑 kubelet 配置文件 /etc/sysconfig/kubelet
# vim /etc/sysconfig/kubelet
KUBELET_EXTRA_ARGS= --tls-cipher-suites=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
重启生效
# systemctl restart kubelet
成果检验
各组件服务整改完毕后,再使用nmap进行扫描,看是否还有DES加密套件。
Etcd
[root@kube-master-1 ~]# nmap --script ssl-enum-ciphers 127.0.0.1 -p 2379
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-10 11:37 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00010s latency).
PORT STATE SERVICE
2379/tcp open etcd-client
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| compressors:
| NULL
| cipher preference: client
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 0.34 seconds
[root@kube-master-1 ~]# nmap --script ssl-enum-ciphers 172.20.200.21 -p 2380
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-10 13:45 CST
Nmap scan report for kube-master-1 (172.20.200.21)
Host is up (0.000087s latency).
PORT STATE SERVICE
2380/tcp open etcd-server
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| compressors:
| NULL
| cipher preference: client
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 0.36 seconds
APIServer
[root@kube-master-1 ~]# nmap --script ssl-enum-ciphers 127.0.0.1 -p 6443
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-10 13:16 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000099s latency).
PORT STATE SERVICE
6443/tcp open sun-sr-https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| compressors:
| NULL
| cipher preference: client
| TLSv1.3:
| ciphers:
| TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| cipher preference: client
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 0.37 seconds
Controller-Manager
[root@kube-master-1 ~]# nmap --script ssl-enum-ciphers 127.0.0.1 -p 10257
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-10 13:41 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000099s latency).
PORT STATE SERVICE
10257/tcp open unknown
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| compressors:
| NULL
| cipher preference: client
| TLSv1.3:
| ciphers:
| TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| cipher preference: client
|_ least strength: A
Scheduler
# nmap --script ssl-enum-ciphers 127.0.0.1 -p 10259
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-10 13:42 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000076s latency).
PORT STATE SERVICE
10259/tcp open unknown
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| compressors:
| NULL
| cipher preference: server
| TLSv1.3:
| ciphers:
| TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| cipher preference: server
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 0.37 seconds
kubelet
[root@kube-master-1 ~]# nmap --script ssl-enum-ciphers 127.0.0.1 -p 10250
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-10 13:36 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000097s latency).
PORT STATE SERVICE
10250/tcp open unknown
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| compressors:
| NULL
| cipher preference: server
| TLSv1.3:
| ciphers:
| TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| cipher preference: server
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 0.36 seconds




